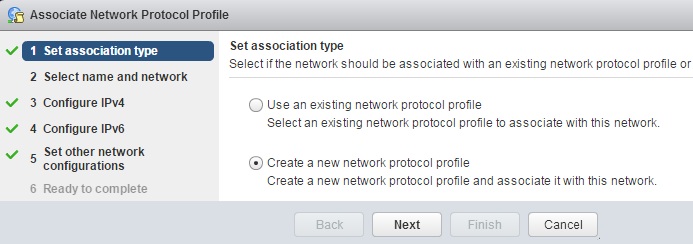
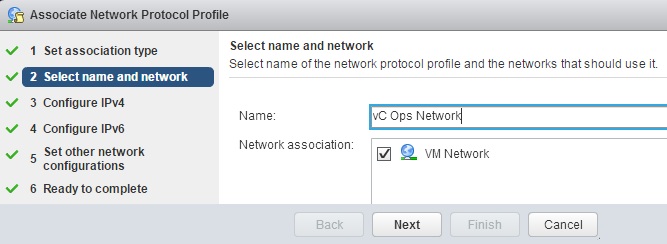
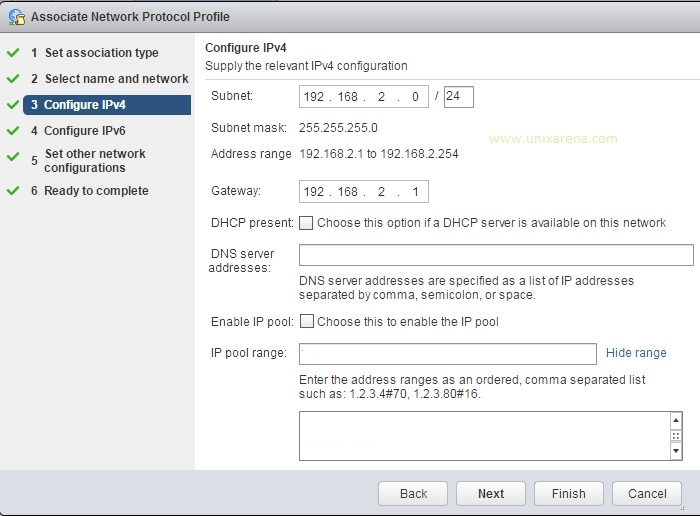
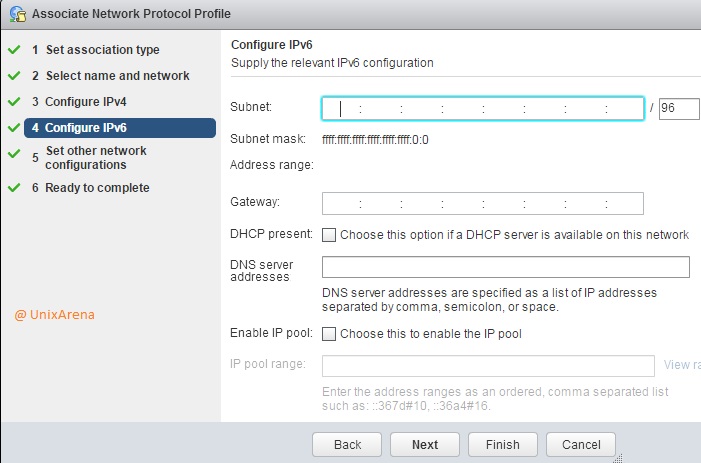
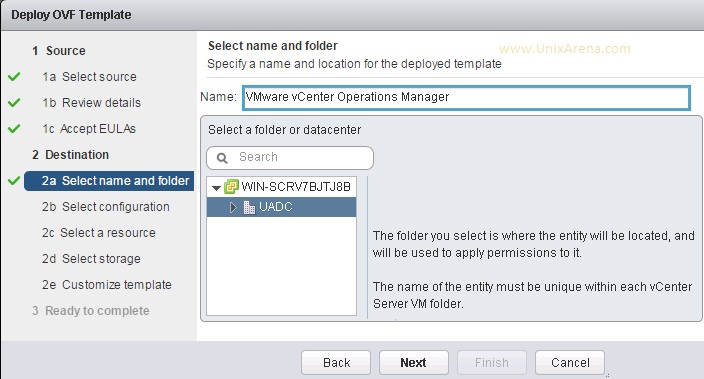
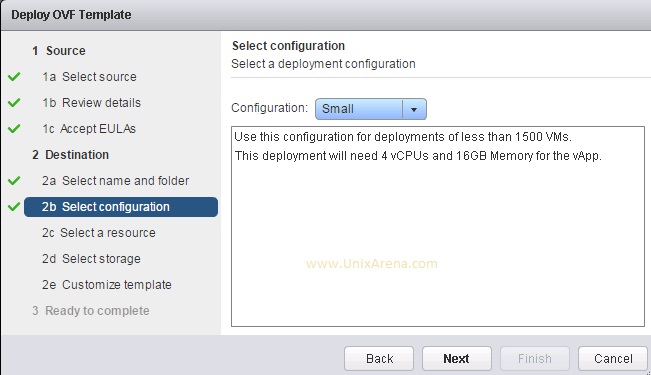
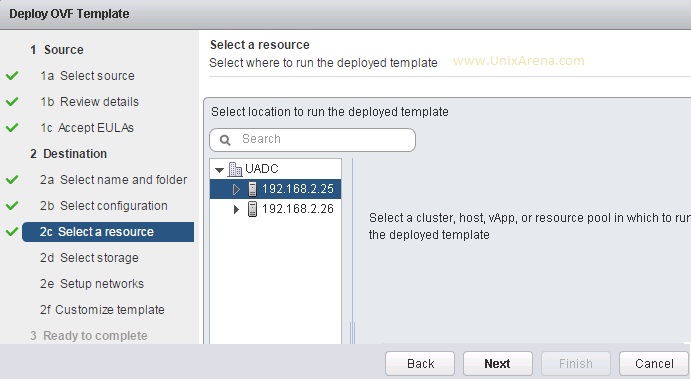
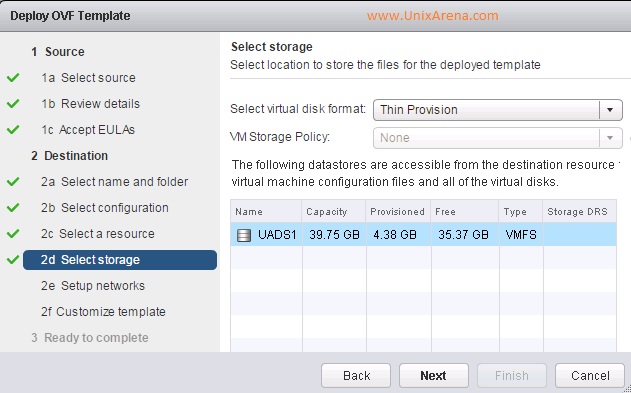
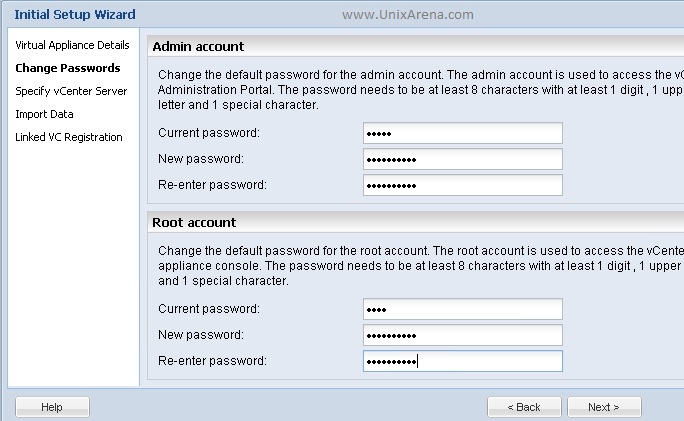
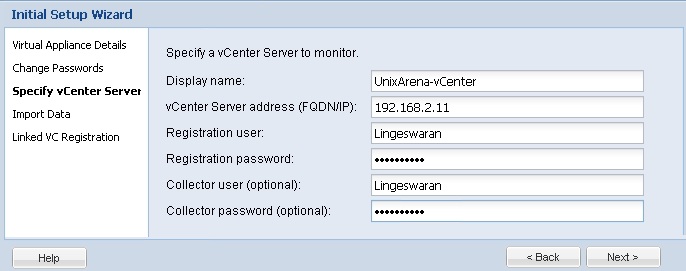
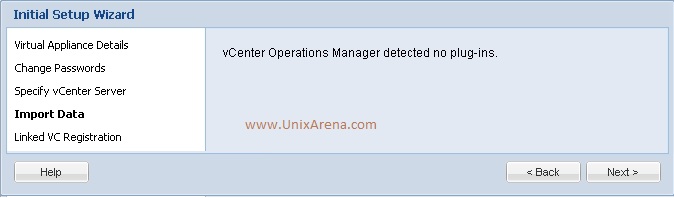
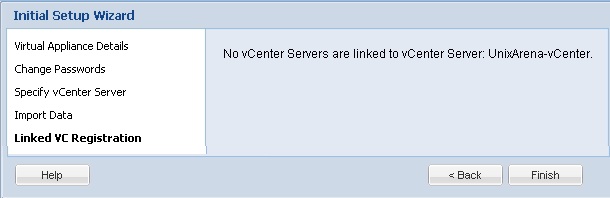
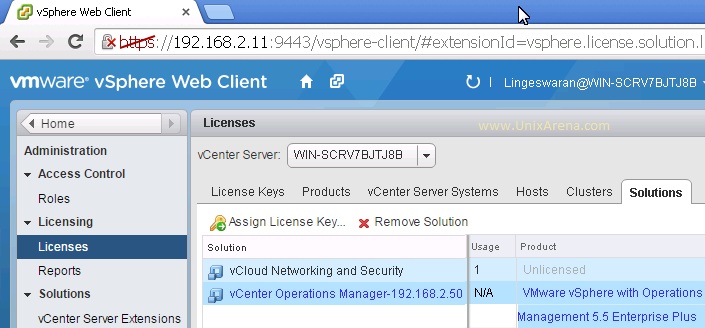
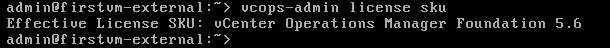
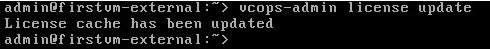
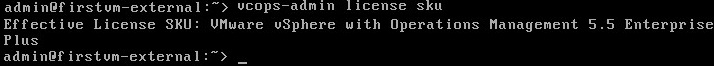
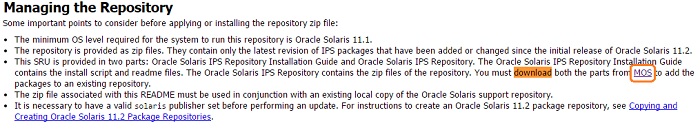
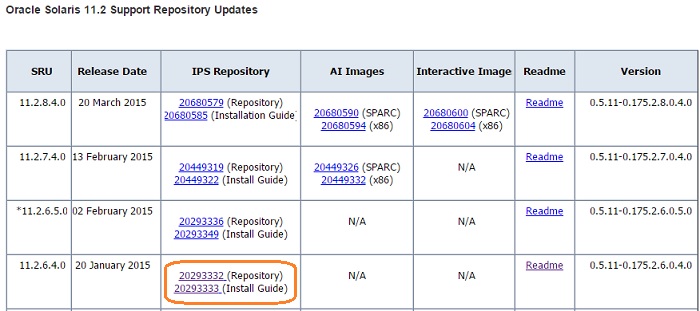
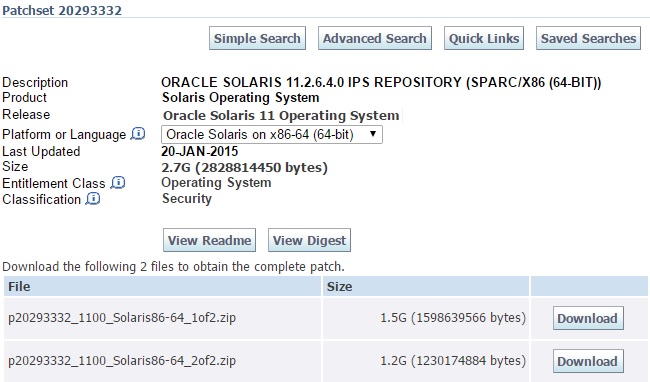
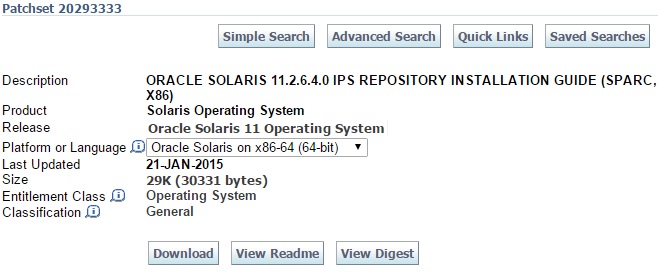
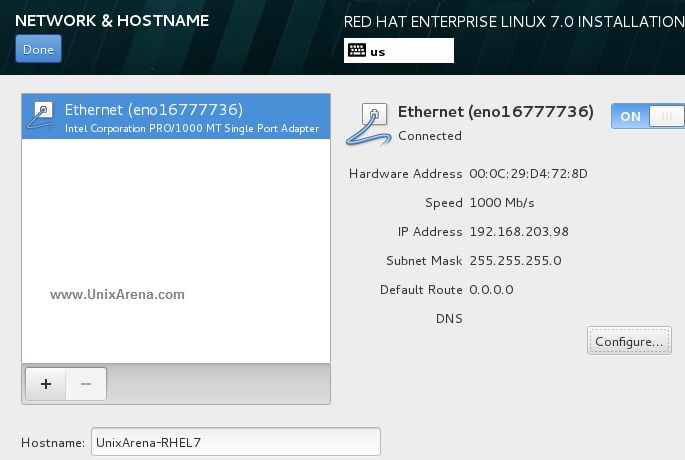
Prior to Redhat Enterprise Linux 7 operating system, init was the process which is responsible for activating the other services in the system. There were daemons and many system V LSB scripts were started at the boot time. These are mostly likely the shell scripts which resides under the /etc/init.d directory and called on the different run levels. But this system has lot of limitation which has been addressed on RHEL 7, with the new init system called “systemd” . In Redhat Enterprise Linux 7 , Systemd owns the process ID 1 .
Highlights of systemd:
- It supports the Parallelization which increases the system boot time.
- Systemd creates the sockets for each daemons and it just needs to connect to the sockets.
- Automatic service dependency management which can prevent long time-outs.
- A method of tacking related processes together by using Linux control groups.
- Still RHEL 7 supports the shell scripts for few legacy services.(/etc/init.d).
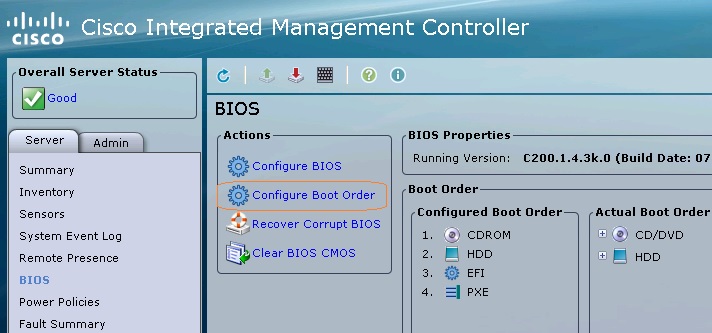
Systemctl :
The systemctl is a command to manage the different type of objects. These objects are called “units” . If you would like to know the available units on RHEl 7 , use the below command.
UA-RHEL7#systemctl -t help
Available unit types:
service
socket
target
device
mount
automount
snapshot
timer
swap
path
slice
scope
UA-RHEL7#
In this article ,we will see about the Service units and Socket units.
Service Management with systemctl:
1. To list all the available services on the system, use the below command.
UA-RHEL7#systemctl --type=service
UNIT LOAD ACTIVE SUB DESCRIPTION
abrt-ccpp.service loaded active exited Install ABRT coredump hook
abrt-oops.service loaded active running ABRT kernel log watcher
abrt-xorg.service loaded active running ABRT Xorg log watcher
abrtd.service loaded active running ABRT Automated Bug Reporting Tool
accounts-daemon.service loaded active running Accounts Service
<<<<<<some lines are truncated>>>>>>>>
udisks2.service loaded active running Disk Manager
upower.service loaded active running Daemon for power management
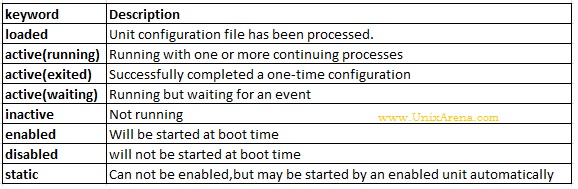
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
64 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
UA-RHEL7#
2. To check the specific service status ,
UA-RHEL7#systemctl status upower.service
upower.service - Daemon for power management
Loaded: loaded (/usr/lib/systemd/system/upower.service; disabled)
Active: active (running) since Thu 2015-04-16 18:59:46 IST; 5h 9min ago
Docs: man:upowerd(8)
Main PID: 1342 (upowerd)
CGroup: /system.slice/upower.service
└─1342 /usr/libexec/upowerd
Apr 16 18:59:46 foundation1.example.com systemd[1]: Starting Daemon for power management...
Apr 16 18:59:46 foundation1.example.com systemd[1]: Started Daemon for power management.
UA-RHEL7#
Here is the another example .
UA-RHEL7#systemctl status sshd.service
sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled)
Active: active (running) since Thu 2015-04-16 18:59:34 IST; 5h 11min ago
Process: 882 ExecStartPre=/usr/sbin/sshd-keygen (code=exited, status=0/SUCCESS)
Main PID: 889 (sshd)
CGroup: /system.slice/sshd.service
└─889 /usr/sbin/sshd -D
Apr 16 18:59:34 foundation1.example.com systemd[1]: Started OpenSSH server daemon.
Apr 16 18:59:35 foundation1.example.com sshd[889]: Server listening on 0.0.0.0 port 22.
Apr 16 18:59:35 foundation1.example.com sshd[889]: Server listening on :: port 22.
Apr 16 22:23:27 foundation1.example.com sshd[6842]: Accepted password for root from 172.25.2.190 port 53230 ssh2
UA-RHEL7#
3.To list the active state of all loaded units, use the below command.
UA-RHEL7#systemctl list-units --type=service
UNIT LOAD ACTIVE SUB DESCRIPTION
abrt-ccpp.service loaded active exited Install ABRT coredump hook
abrt-oops.service loaded active running ABRT kernel log watcher
abrt-xorg.service loaded active running ABRT Xorg log watcher
abrtd.service loaded active running ABRT Automated Bug Reporting Tool
accounts-daemon.service loaded active running Accounts Service
atd.service loaded active running Job spooling tools
auditd.service loaded active running Security Auditing Service
avahi-daemon.service loaded active running Avahi mDNS/DNS-SD Stack
4. To list the active and inactive state of all loaded units, use the below command.
UA-RHEL7#systemctl list-units --type=service -all
UNIT LOAD ACTIVE SUB DESCRIPTION
abrt-ccpp.service loaded active exited Install ABRT coredump hook
abrt-oops.service loaded active running ABRT kernel log watcher
abrt-vmcore.service loaded inactive dead Harvest vmcores for ABRT
abrt-xorg.service loaded active running ABRT Xorg log watcher
abrtd.service loaded active running ABRT Automated Bug Reporting Tool
accounts-daemon.service loaded active running Accounts Service
atd.service loaded active running Job spooling tools
auditd.service loaded active running Security Auditing Service
avahi-daemon.service loaded active running Avahi mDNS/DNS-SD Stack
UA-RHEL7#
5.The below command will help you that whether the service will be started automatically or not .
UA-RHEL7#systemctl list-unit-files --type=service
UNIT FILE STATE
abrt-ccpp.service enabled
abrt-oops.service enabled
abrt-pstoreoops.service disabled
abrt-vmcore.service enabled
abrt-xorg.service enabled
abrtd.service enabled
accounts-daemon.service enabled
anaconda-direct.service static
anaconda-noshell.service static
anaconda-shell@.service static
anaconda-sshd.service static
anaconda-tmux@.service static
anaconda.service static
arp-ethers.service disabled
atd.service enabled
auditd.service enabled
autofs.service disabled
autovt@.service disabled
avahi-daemon.service enabled
![service status in RHEL7]()
service status in RHEL7
6. You can filter the failed services using the systemctl command with below mentioned options.
UA-RHEL7#systemctl --failed --type=service
UNIT LOAD ACTIVE SUB DESCRIPTION
rhnsd.service loaded failed failed LSB: Starts the Spacewalk Daemon
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
1 loaded units listed. Pass --all to see loaded but inactive units, too.
To show all installed unit files use 'systemctl list-unit-files'.
UA-RHEL7#
7. To list the all sockets units on the system,
UA-RHEL7#systemctl list-units --type=socket --all
UNIT LOAD ACTIVE SUB DESCRIPTION
avahi-daemon.socket loaded active running Avahi mDNS/DNS-SD Stack Activation Socket
dbus.socket loaded active running D-Bus System Message Bus Socket
dm-event.socket loaded active listening Device-mapper event daemon FIFOs
iscsid.socket loaded active listening Open-iSCSI iscsid Socket
iscsiuio.socket loaded active listening Open-iSCSI iscsiuio Socket
lvm2-lvmetad.socket loaded active running LVM2 metadata daemon socket
rpcbind.socket loaded active running RPCbind Server Activation Socket
syslog.socket loaded inactive dead Syslog Socket
systemd-initctl.socket loaded active listening /dev/initctl Compatibility Named Pipe
systemd-journald.socket loaded active running Journal Socket
systemd-shutdownd.socket loaded active listening Delayed Shutdown Socket
systemd-udevd-control.socket loaded active running udev Control Socket
systemd-udevd-kernel.socket loaded active running udev Kernel Socket
LOAD = Reflects whether the unit definition was properly loaded.
ACTIVE = The high-level unit activation state, i.e. generalization of SUB.
SUB = The low-level unit activation state, values depend on unit type.
13 loaded units listed.
To show all installed unit files use 'systemctl list-unit-files'.
UA-RHEL7#
Controlling the services with systemctl :
1. Check the crond service status.
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled)
Active: active (running) since Thu 2015-04-16 18:59:30 IST; 5h 54min ago
Main PID: 793 (crond)
CGroup: /system.slice/crond.service
└─793 /usr/sbin/crond -n
Apr 16 18:59:30 foundation1.example.com systemd[1]: Started Command Scheduler.
Apr 16 18:59:31 foundation1.example.com crond[793]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 40% if used.)
Apr 16 18:59:31 foundation1.example.com crond[793]: (CRON) INFO (running with inotify support)
UA-RHEL7#
2. To stop the service , use systemctl stop command.
UA-RHEL7#systemctl stop crond.service
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled)
Active: inactive (dead) since Fri 2015-04-17 00:56:06 IST; 1s ago
Process: 793 ExecStart=/usr/sbin/crond -n $CRONDARGS (code=exited, status=0/SUCCESS)
Main PID: 793 (code=exited, status=0/SUCCESS)
Apr 16 18:59:30 foundation1.example.com systemd[1]: Started Command Scheduler.
Apr 16 18:59:31 foundation1.example.com crond[793]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 40% if used.)
Apr 16 18:59:31 foundation1.example.com crond[793]: (CRON) INFO (running with inotify support)
Apr 17 00:56:06 foundation1.example.com systemd[1]: Stopping Command Scheduler...
Apr 17 00:56:06 foundation1.example.com systemd[1]: Stopped Command Scheduler.
UA-RHEL7#
3.Service can be started back using systemctl start command.
UA-RHEL7#systemctl start crond.service
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled)
Active: active (running) since Fri 2015-04-17 01:04:52 IST; 1s ago
Main PID: 9694 (crond)
CGroup: /system.slice/crond.service
└─9694 /usr/sbin/crond -n
Apr 17 01:04:52 foundation1.example.com systemd[1]: Started Command Scheduler.
Apr 17 01:04:52 foundation1.example.com crond[9694]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 41% if used.)
Apr 17 01:04:52 foundation1.example.com crond[9694]: (CRON) INFO (running with inotify support)
Apr 17 01:04:52 foundation1.example.com crond[9694]: (CRON) INFO (@reboot jobs will be run at computer's startup.)
UA-RHEL7#
4.Specific service can be restarted using “systemctl restart” command.
UA-RHEL7#systemctl restart crond.service
UA-RHEL7#echo $?
0
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled)
Active: active (running) since Fri 2015-04-17 01:05:35 IST; 10s ago
Main PID: 9708 (crond)
CGroup: /system.slice/crond.service
└─9708 /usr/sbin/crond -n
5. If you use the restart command , process ID will be changed. But if you use “reload” option, it re-reads the configuration without a complete stop and start. So the process ID remains same.
UA-RHEL7#systemctl status sshd.service |head -8
sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled)
Active: active (running) since Thu 2015-04-16 18:59:34 IST; 6h ago
Process: 882 ExecStartPre=/usr/sbin/sshd-keygen (code=exited, status=0/SUCCESS)
Main PID: 889 (sshd)
CGroup: /system.slice/sshd.service
└─889 /usr/sbin/sshd -D
UA-RHEL7#systemctl reload sshd.service
UA-RHEL7#systemctl status sshd.service |head -8
sshd.service - OpenSSH server daemon
Loaded: loaded (/usr/lib/systemd/system/sshd.service; enabled)
Active: active (running) since Thu 2015-04-16 18:59:34 IST; 6h ago
Process: 9853 ExecReload=/bin/kill -HUP $MAINPID (code=exited, status=0/SUCCESS)
Process: 882 ExecStartPre=/usr/sbin/sshd-keygen (code=exited, status=0/SUCCESS)
Main PID: 889 (sshd)
CGroup: /system.slice/sshd.service
└─889 /usr/sbin/sshd -D
UA-RHEL7#
6. To see the service dependency tree , use the below command.
UA-RHEL7#systemctl list-dependencies crond.service
crond.service
├─system.slice
└─basic.target
├─microcode.service
├─rhel-autorelabel-mark.service
├─rhel-autorelabel.service
├─rhel-configure.service
├─rhel-dmesg.service
├─rhel-loadmodules.service
├─paths.target
├─slices.target
│ ├─-.slice
│ └─system.slice
├─sockets.target
│ ├─avahi-daemon.socket
│ ├─dbus.socket
│ ├─dm-event.socket
│ ├─iscsid.socket
│ ├─iscsiuio.socket
│ ├─lvm2-lvmetad.socket
│ ├─rpcbind.socket
│ ├─systemd-initctl.socket
│ ├─systemd-journald.socket
│ ├─systemd-shutdownd.socket
│ ├─systemd-udevd-control.socket
│ └─systemd-udevd-kernel.socket
├─sysinit.target
│ ├─dev-hugepages.mount
│ ├─dev-mqueue.mount
│ ├─dmraid-activation.service
│ ├─iscsi.service
│ ├─kmod-static-nodes.service
│ ├─lvm2-monitor.service
│ ├─multipathd.service
│ ├─plymouth-read-write.service
│ ├─plymouth-start.service
│ ├─proc-sys-fs-binfmt_misc.automount
│ ├─sys-fs-fuse-connections.mount
│ ├─sys-kernel-config.mount
│ ├─sys-kernel-debug.mount
│ ├─systemd-ask-password-console.path
│ ├─systemd-binfmt.service
│ ├─systemd-journal-flush.service
│ ├─systemd-journald.service
│ ├─systemd-modules-load.service
│ ├─systemd-random-seed.service
│ ├─systemd-sysctl.service
│ ├─systemd-tmpfiles-setup-dev.service
│ ├─systemd-tmpfiles-setup.service
│ ├─systemd-udev-trigger.service
│ ├─systemd-udevd.service
│ ├─systemd-update-utmp.service
│ ├─systemd-vconsole-setup.service
│ ├─cryptsetup.target
│ ├─local-fs.target
│ │ ├─-.mount
│ │ ├─rhel-import-state.service
│ │ ├─rhel-readonly.service
│ │ ├─systemd-fsck-root.service
│ │ └─systemd-remount-fs.service
│ └─swap.target
│ ├─dev-disk-by\x2dpath-pci\x2d0000:00:10.0\x2dscsi\x2d0:0:0:0\x2dpart2.swap
│ ├─dev-disk-by\x2duuid-5926a1d5\x2dc610\x2d4b3a\x2da63b\x2d17dd34a4da6f.swap
│ ├─dev-disk-by\x2duuid-5926a1d5\x2dc610\x2d4b3a\x2da63b\x2d17dd34a4da6f.swap
│ └─dev-sda2.swap
└─timers.target
└─systemd-tmpfiles-clean.timer
UA-RHEL7#
7. To prevent the service from starting at the boot time , use systemctl disable command.
UA-RHEL7#systemctl disable crond.service
rm '/etc/systemd/system/multi-user.target.wants/crond.service'
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; disabled)
Active: active (running) since Fri 2015-04-17 01:05:35 IST; 13min ago
Main PID: 9708 (crond)
CGroup: /system.slice/crond.service
└─9708 /usr/sbin/crond -n
The same way , if you want to start the specific service at the system boot time, use systemctl enable command.
UA-RHEL7#systemctl enable crond.service
ln -s '/usr/lib/systemd/system/crond.service' '/etc/systemd/system/multi-user.target.wants/crond.service'
UA-RHEL7#systemctl status crond.service
crond.service - Command Scheduler
Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled)
Active: active (running) since Fri 2015-04-17 01:05:35 IST; 14min ago
Main PID: 9708 (crond)
CGroup: /system.slice/crond.service
└─9708 /usr/sbin/crond -n
8. To disable the service permanently , use “systemctl mask” command.
UA-RHEL7#systemctl mask crond.service
ln -s '/dev/null' '/etc/systemd/system/crond.service'
UA-RHEL7#systemctl status crond.service
crond.service
Loaded: masked (/dev/null)
Active: active (running) since Fri 2015-04-17 01:05:35 IST; 16min ago
Main PID: 9708 (crond)
CGroup: /system.slice/crond.service
└─9708 /usr/sbin/crond -n
The disabled service will not be started automatically at boot but it can be started manually. A masked service will not be started manually or automatically.
Let me try to stop and start the service which is masked currently.
UA-RHEL7#systemctl stop crond.service
UA-RHEL7#systemctl start crond.service
Failed to issue method call: Unit crond.service is masked.
UA-RHEL7#systemctl status crond.service
crond.service
Loaded: masked (/dev/null)
Active: inactive (dead) since Fri 2015-04-17 01:23:53 IST; 11s ago
Main PID: 9708 (code=exited, status=0/SUCCESS)
I felt that systemctl is almost similar to SMF in oracle Solaris 10 /11.
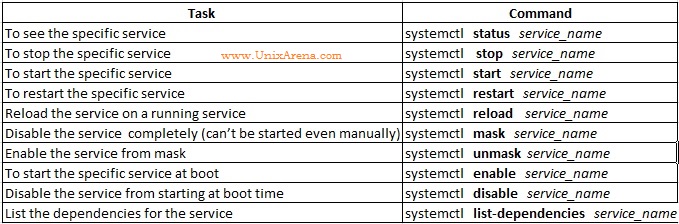
systemctl – cheat sheet:
![systemctl - RHEL7]()
systemctl – RHEL7
Hope this article is informative to you .
Share it ! Comment it !! Be Sociable !!!
The post Service Management (systemd) – RHEL 7 appeared first on UnixArena.